Dispersed Forswearing of Administration (DDoS) assaults have arisen as quite possibly the most predominant danger in the computerized scene. These assaults can upset administrations, cripple associations, and cause critical monetary misfortunes. This thorough aid dives into the complexities of DDoS assaults, investigating their components, types, verifiable settings, influences on organizations and people, and procedures for alleviation. Distributed Denial-of-Service (DDoS)
What is a DDoS Attack?
Definition of DDoS
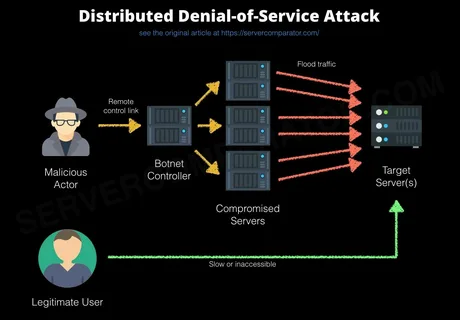
A Conveyed Refusal of Administration (DDoS) assault is a malevolent endeavor to disturb the typical working of a designated server, administration, or organization by overpowering it with a surge of Web traffic. In contrast to a standard Forswearing of Administration (DoS) assault that begins from a solitary source, a DDoS assault involves numerous compromised PC frameworks as wellsprings of traffic.
How DDoS Attacks Work Distributed Denial-of-Service (DDoS)
DDoS goes after ordinarily includes three primary parts:
- Assailant: The individual or gathering coordinating the assault.
- Botnet: An organization of compromised gadgets (frequently alluded to as “zombies”) that are constrained by the assailant. These gadgets can incorporate PCs, IoT gadgets, and servers.
- Focus on: The framework or organization that is being gone after.
The aggressor orders the botnet to send a staggering measure of traffic to the objective, making it delayed or totally inaccessible to real clients.
Types of DDoS Attacks
DDoS assaults can be arranged into a few classes in light of their techniques and targets. Understanding these sorts is critical for compelling guard procedures.
1. Volumetric Attacks
Volumetric assaults intend to consume the data transfer capacity of the objective organization or administration. These assaults produce enormous measures of traffic to overpower the objective’s ability.
- Models:
- UDP Flood: Sends a lot of Client Datagram Convention (UDP) bundles to irregular ports on an objective server.
- ICMP Flood: Uses Web Control Message Convention (ICMP) bundles to flood the objective with demands.
2. Protocol Attacks Distributed Denial-of-Service (DDoS)
Convention assaults exploit shortcomings in network conventions. They intend to consume server assets or moderate correspondence gear like firewalls and burden balancers.
- Models:
- SYN Flood: Starts an association with an objective server but never finishes it, prompting asset weariness.
- Ping of Death: Sends contorted or larger-than-average bundles to crash the objective framework.
3. Application Layer Attacks
Application layer assaults target explicit applications or administrations by sending demands that seem authentic but are intended to deplete assets.
- Models:
- HTTP Flood: Sends various HTTP solicitations to overpower web servers.
- Slowloris: Keeps numerous associations open by sending fractional HTTP demands, consuming server assets without creating critical traffic.
Historical Context of DDoS Attacks Distributed Denial-of-Service (DDoS)
Early Days of DDoS Attacks
The idea of disavowal of administration assaults traces all the way back to the beginning of the Web. The principal realized the DoS assault happened in 1996 against Panix, a Web access supplier in New York. Nonetheless, it was only after the last part of the 1990s and mid-2000s that DDoS assaults acquired reputation.
Notable Incidents
- Mafiaboy Assault (2000): A young person named Michael Calce sent off an enormous DDoS assault against a few high-profile sites, including CNN and eBay. This occurrence featured the weakness of large companies to such assaults.
- Estonia Cyberattacks (2007): Following political strains with Russia, Estonia encountered a progression of DDoS assaults that designated government and monetary sites, disturbing administrations across the country.
- Moreover Dyn Assault (2016): A gigantic DDoS assault on Dyn, a significant DNS supplier, disturbed admittance to various famous sites like Twitter and Netflix. This assault was outstanding for its utilization of IoT gadgets as a component of a botnet.

The Effect of DDoS Assaults
DDoS attacks can have extensive repercussions for associations and individuals the equivalent.
Financial Losses
Then the quick effect of a DDoS assault frequently appears as monetary misfortunes because of margin time and lost income open doors. Associations might confront costs connected with:
- Moderation Endeavors: Putting resources into security arrangements and administrations post-assault.
- Notoriety Harm: Loss of client trust can prompt long-haul monetary repercussions.
Operational Disruption
DDoS assaults can disturb ordinary business activities:
- Administration Blackouts: Clients might not be able to get to administrations during an assault.
- Moreover asset Channel: IT groups might be redirected from other basic undertakings to address the continuous assault.
Legal Ramifications
Associations might confront legitimate outcomes on the off chance that they neglect to safeguard delicate client information during an assault:
- Moreover consistency Infringement: Administrative bodies might force fines for neglecting to sufficiently get information.
- Moreover suit Dangers: Impacted clients might seek lawful activity against associations for neglecting to offer continuous assistance.
Mitigating DDoS Attacks
While it is difficult to wipe out all dangers related to DDoS assaults, associations can execute different systems to relieve their effect.
1. Implementing Robust Security Measures
Associations ought to take on complete safety efforts that include:
- Moreover firewalls: Use progressed firewalls fit for sifting through malevolent traffic.
- Moreover interruption Identification Frameworks (IDS): Screen network traffic for dubious action and ready directors.
2. Utilizing DDoS Protection Services Distributed Denial-of-Service (DDoS)
Moreover, many specialist organizations offer particular DDoS security benefits that can assimilate and alleviate enormous scope assaults:
- Moreover cloud-Based Arrangements: These administrations can scale progressively founded on traffic volume.
- Moreover content Conveyance Organizations (CDNs): CDNs assist with dispersing traffic across different servers, decreasing the burden on any single point.
3. Developing an Incident Response Plan Distributed Denial-of-Service (DDoS)
Associations ought to get ready for potential DDoS episodes by making an occurrence reaction plan that layouts:
- Jobs and Obligations: Characterize who will deal with the reaction during an assault.
- Moreover correspondence Conventions: Lay out clear correspondence channels for interior groups and outside partners.
4. Regular Security Audits and Testing of Distributed Denial-of-Service (DDoS)
Leading ordinary security reviews distinguishes weaknesses inside an association’s foundation:
- Moreover infiltration Testing: Mimic potential assault situations to survey guards.
- Weakness Appraisals: Consistently filter frameworks for shortcomings that could be taken advantage of during an assault.
The Future of DDoS Attacks
As innovation develops, so do the strategies utilized by aggressors. A few arising patterns include:
Increased Use of IoT Devices Distributed Denial-of-Service (DDoS)
The multiplication of Web of Things (IoT) gadgets has set out new open doors for assailants:
- Moreover, numerous IoT gadgets need vigorous safety efforts, making them obvious objectives for botnets.
The weaponization of AI and Machine Learning Distributed Denial-of-Service (DDoS)
Aggressors are progressively utilizing man-made consciousness (artificial intelligence) and AI procedures:
- These advances empower versatile assaults that can sidestep conventional guards more successfully than previously.
Focus on Data Theft During Attacks
DDoS assaults are progressively being utilized as distractions for additional complex cybercrimes:
- While diverting security groups with administration interruptions, aggressors may at the same time endeavor information breaks or malware infusions.
Conclusion
Moreover, dispersed Forswearing of Administration (DDoS) assaults address a critical danger in the present computerized scene. Moreover grasping their components, types, verifiable settings, influences on organizations and people, and viable alleviation methodologies is critical for associations meaning to safeguard themselves from these troublesome occasions. As innovation keeps on developing, so should our guards against these undeniably refined dangers. By putting resources into strong safety efforts and planning for likely occurrences, associations can limit their gamble openness and guarantee business progression notwithstanding advancing digital dangers. Distributed Denial-of-Service (DDoS)
Citations:
https://www.netscout.com/what-is-ddos
https://www.micromindercs.com/blog/the-future-of-ddos-security-navigating-evolving-techniques
https://www.esecurityplanet.com/networks/types-of-ddos-attacks/
https://nsfocusglobal.com/2024-global-ddos-attack-trends-insights-challenges-and-defense-strategies/
https://cybersecurity-magazine.com/the-history-and-future-of-ddos-attacks/
https://en.wikipedia.org/wiki/Distributed_denial-of-service_attack